今天在先知社区阅读代码审计技巧,无意发现一个之前没怎么接触过的漏洞------PHP_SELF漏洞,于是决定学习一些这个漏洞的原理,找到了一篇比较好理解的文章,作为一个转载吧。
http://www.yourserver.com/form-action.php
http://www.yourserver.com/dir1/form-action.php
<form method="post" action="form-action.php" >
我们可以使用PHP_SELF变量而不是“form-action.php”。代码变成:
<form name="form1" method="post" action="<?php echo $_SERVER[‘PHP_SELF‘]; ?>" >
<?php
if(isset($_POST[‘submit‘]))
{
$name = $_POST[‘name‘];
echo "User Has submitted the form and entered this name : <b> $name </b>";
echo "<br>You can use the following form again to enter a new name.";
}
?>
<form method="post" action="<?php echo $_SERVER[‘PHP_SELF‘]; ?>"> //php代码优先于HTML执行
<input type="text" name="name"><br>
<input type="submit" name="submit" value="Submit Form"><br>
</form>
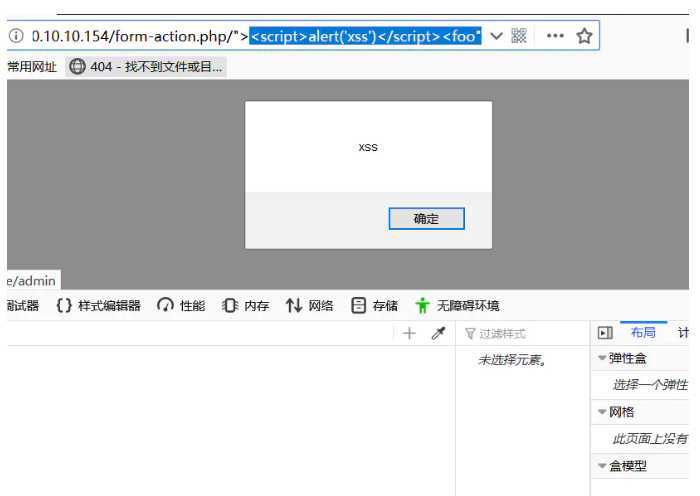
http://www.yourdomain.com/form-action.php/"><script>alert(‘xss‘)</script><foo"
<form name="test" method="post" action="form-action.php"/> <script>alert(‘xss‘)</script><foo"">
原文:https://www.cnblogs.com/Qiuzhiyu/p/13121420.html