截包,改一下cookie发现加密前的cookie结构:
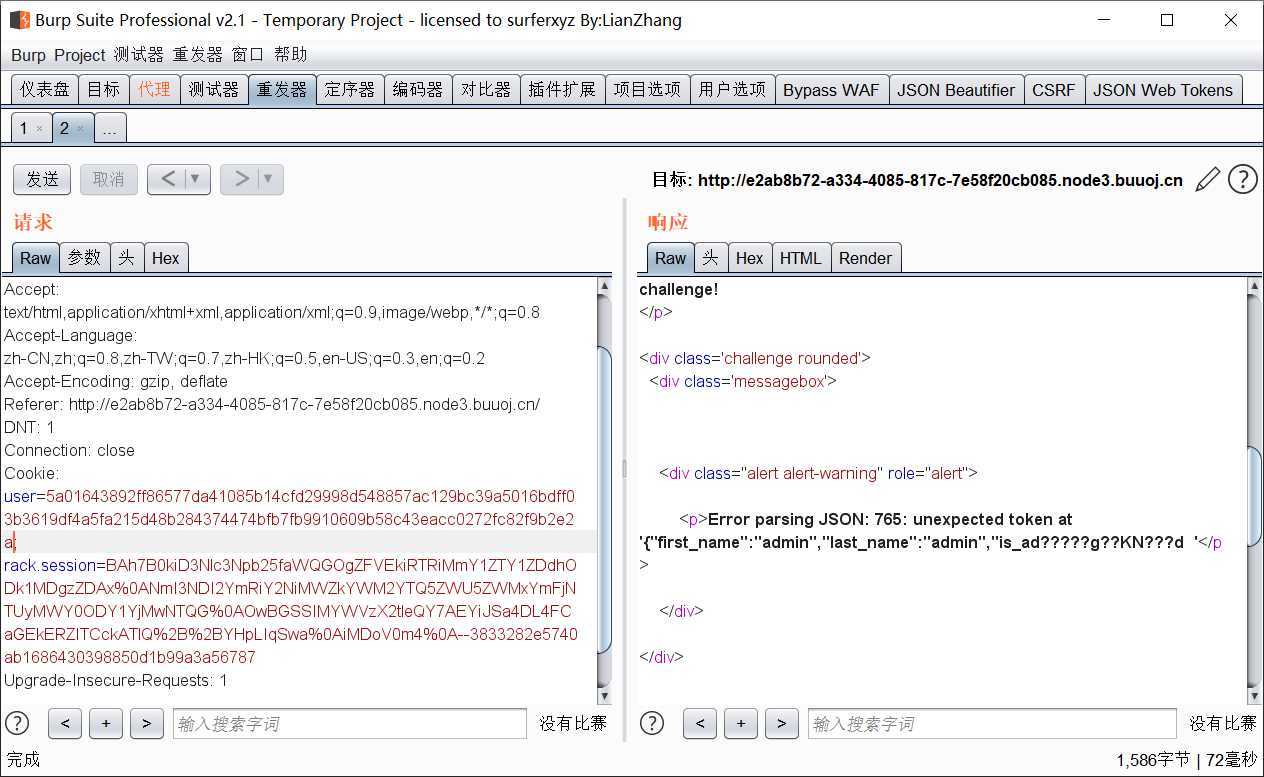
原结构应为:{"first_name":"admin","last_name":"admin","is_admin":0}(cookie中的user值最后一位从e改成了a)
是CBC加密的特征,此处构造攻击使is_admin:1,具体攻击方法可参考:CBC具体攻击方法及原理
尝试整块替换:{"first_name":"A1.00000000000000","last_name":"hhhh","is_admin":0}
每十六位一块,加密后用十六进制表示因此每块32位
{"first_name":"A
1.00000000000000
","last_name":"h
hhh","is_admin":
0}?
cookie:
<!--为了便于观察,原为一行--> 9dd9501454f1d5ee3ee1b6c392863e33 a1a082b3710ac40c387e2adabbf2c080 97f0e38bf04de0fe1ac716a3f8a62592 5b39faa2b376c9209346af961f0f92ff 365ab185ebe5567c577aaa630787ee19
由于CBC是分块加密,因此只要保正一次替换一整块的内容,就能够正常解析,此时将加密后的第二块内容加到倒数第二块
9dd9501454f1d5ee3ee1b6c392863e33 // {"first_name":"A
a1a082b3710ac40c387e2adabbf2c080 // 1.00000000000000
97f0e38bf04de0fe1ac716a3f8a62592 // ","last_name":"h
5b39faa2b376c9209346af961f0f92ff // hhh","is_admin":
a1a082b3710ac40c387e2adabbf2c080 // 1.00000000000000
365ab185ebe5567c577aaa630787ee19 // 0}
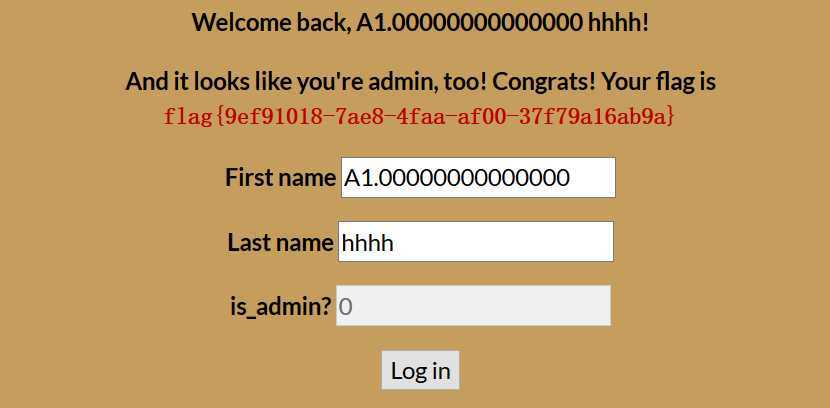
这时cookie实际为:{"first_name":"A1.00000000000000","last_name":"hhhh","is_admin":1.000000000000000},就能够满足题目要求
cookie = ‘9dd9501454f1d5ee3ee1b6c392863e33a1a082b3710ac40c387e2adabbf2c08097f0e38bf04de0fe1ac716a3f8a625925b39faa2b376c9209346af961f0f92ff365ab185ebe5567c577aaa630787ee19‘ a = cookie[:-32]+cookie[32:64]+cookie[-32:]
By Wander
原文:https://www.cnblogs.com/neu-cdr/p/13049203.html